Bitcoin wallets are designed to hold and manage the private keys associated with your bitcoin holdings. These private keys are critical for accessing and spending your funds, so what would stop a wallet from stealing your bitcoin without your knowledge? Can bitcoin be stolen from your wallet? How do you ensure that your wallet is secure?
- Use an open-source wallet such as Samourai, Mycellium, Wasabi and Electrum
- Use a hardware wallet, preferably called signing device, such as Trezor to make sure your private keys aren’t available in an internet-connected device
- Use two-factor authentication (2FA) for your wallet whenever possible to add an extra layer of security by requiring a second form of verification
- Keep your device clean, updated and secure, don’t use Windows. Find out the best operating system for bitcoin storage
Open source
- Lindy effect, older is better, Electrum is quite a good choice
- Use Wallet Scrutiny to analyze transparency and security of Android wallets
- Verify GPG and/or SHA hashes
How to verify GPG signatures
GPG stands for GNU Privacy Guard. A GPG signature is a digital signature that may be created by anybody who has access to a private GPG key. A GPG signature proves that the files you downloaded were signed by the owner of the GPG key. Therefore, GPG signature verification will ensure the security of your wallet. For instance, when you download Electrum wallet, the file will come along with their GPG signatures (as shown in the image below).
To verify a GPG signature, you will need to have the public key of the signer. You can then use a GPG command-line tool to verify the signature. First, use the gpg command to import the signer’s public key. For example, if the public key is in a file called signer_key.asc, you can import it with the following command:
gpg --import signer_key.asc
Next, use the gpg command to verify the signature file. For example, if the signature file is called signature.asc and the signed file is called signed_file.txt, you can verify the signature with the following GPG command line:
gpg --verify signature.asc signed_file.txt
If the signature is valid, you will see a message indicating that the signature was verified successfully. If the signature is not valid, you will see an error message.
It’s important to note that simply verifying the signature does not guarantee the authenticity of the signed file. To achieve that, you must also trust the signer’s public key. This involves verifying the signer’s identity and ensuring that their key has not been compromised.
How to verify SHA256 or SHA512
To verify the SHA512 hash of a piece of software to validate its integrity, you will need to obtain the correct hash from a trusted source. This could be the software developer or a reputable third-party website.
Once you have the correct SHA512 hash, you can use a cryptographic hash function to generate a hash of the software file and compare it to the provided hash. If the two hashes match, it indicates that the software file is authentic and has not been tampered with.
To generate the hash of a file using the SHA512 algorithm, you can use a command-line tool such as openssl. For example, if the software file is called software.exe, you can generate its SHA512 hash with the following command:
openssl sha512 software.exe
This will output the SHA512 hash of the file. You can then compare this hash to the provided hash to verify the authenticity of the software.
It’s important to note that simply verifying the SHA512 hash does not guarantee the safety of the software. It only guarantees that the file has not been tampered with. You should still carefully evaluate the software and any potential risks before installing and running it on your system.
Hardware wallet
A bitcoin hardware wallet is a physical device that is designed to securely store and manage private keys associated with bitcoin and other cryptocurrencies. These private keys are critical for accessing and spending your funds, so it’s essential to keep them safe.
Using a hardware wallet has several benefits over storing your private keys on a software wallet on your computer or mobile device.
First, a hardware wallet is much more secure than a software wallet because it is not connected to the internet. This makes it much less vulnerable to hacking and other cyberattacks.
Second, a hardware wallet allows you to securely manage your private keys without exposing them to the internet. This means that even if your computer or mobile device is compromised, your funds will still be safe on your hardware wallet.
Third, a hardware wallet is a convenient and easy-to-use way to manage your private keys. It allows you to securely access your funds and sign transactions without having to remember complex private keys or passwords.
A good hardware wallet allows you to verify the transaction outputs. So, you can verify that the addresses on your computer or phone screen match with the addresses shown on the hardware device. (Usually the hardware wallet also knows which address is the change address.)
See these open source hardware wallets:
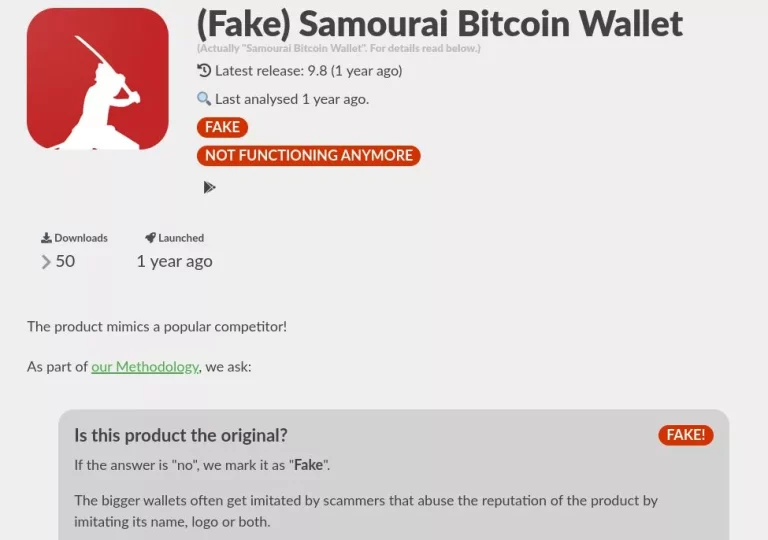
Fake Bitcoin Wallets
To prevent your Bitcoin from being stolen, you need to be aware of fake Bitcoin wallets, which masquerade as real Bitcoin wallets, designed to trick you into depositing your Bitcoin, only to disappear with them. Some of these fake wallets often lure you in with promises of free Bitcoin or high returns on your investment. Once you have deposited your Bitcoin into the wallet, the scammers will disappear with it.
Fake BTC wallets come in various forms, including the following:
- Phishing wallets: These fake wallets mimic the appearance and functionality of legitimate wallets, often through cloned websites or mobile apps. They may lure users through phishing emails or fake ads, tricking them into entering their private keys or seed phrases, which grant the scammer access to their Bitcoin.
- Hardware wallet clones: Counterfeit hardware wallets resembling popular brands like Coldcard, Blockstream Jade, or Trezor might be sold through unofficial channels. These clones might have tampered firmware that steals private keys during the wallet setup process.
- Mobile app malware: Malicious mobile apps disguised as Bitcoin wallets can infect users’ phones and steal private keys stored on the device or clipboard.
- Cloud storage scams: Fake cloud storage services advertised for storing Bitcoin private keys could be traps, designed to steal users’ information once they upload their keys.
Stick to reputable exchanges and wallets with established reputations and clear security protocols. Knowledge is your best defense. Research wallets before using them, read our reviews of legitimate Bitcoin wallets.
Can Stolen Bitcoin Be Recovered?
Recovering stolen Bitcoin is unfortunately very difficult, bordering on impossible in most cases. Here’s why: Firstly, Bitcoin transactions are recorded on a public ledger called the blockchain, and once confirmed, they are irreversible. This means that once your Bitcoin is sent to someone else’s address, it’s out of your hands unless they choose to return it. Secondly, Bitcoin transactions are pseudonymous, meaning that while addresses are publicly visible on the blockchain, the identities of the people behind them are not. This makes it difficult to track down the thief and potentially recover your Bitcoin. Thirdly, unlike traditional financial systems, Bitcoin doesn’t have a central authority like a bank that can intervene and reverse transactions. This means that you’re solely responsible for your Bitcoin and its security. Finally, thieves often use “mixing services” to further obfuscate the trail of stolen Bitcoin. These services blend stolen coins with legitimate ones, making it nearly impossible to pinpoint the origin.
Conclusion
One of the key risks to the security of your wallet is the possibility of malware stealing your private keys. Malware is software that is designed to damage or gain unauthorized access to a computer system, and it can be a major threat to the security of your wallet.
To protect yourself against this threat, it’s important to use an open-source wallet that has been reviewed and verified by the community. This ensures that the code behind the wallet is transparent and can be scrutinized for any potential vulnerabilities.
In addition, using a hardware wallet can provide an extra layer of security. These devices are designed to hold your private keys and sign transactions without exposing them to the internet, making it much more difficult for malware to steal them.
Overall, the best way to protect yourself against the risk of a wallet stealing your bitcoins is to use a secure, open-source wallet and consider using a hardware wallet for added security. By following these steps, you can ensure that your funds are safe and secure.